SAST in your SDLC for Cloud-Native Apps 2
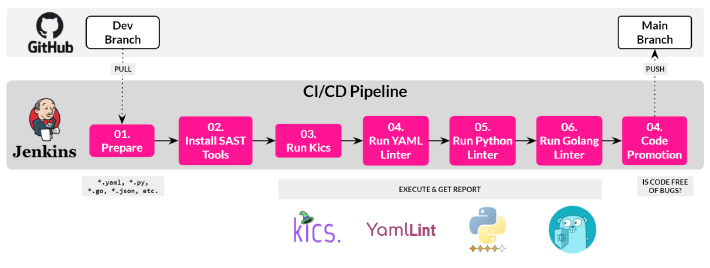
Unlike the previous post, this post will implement a Jenkins Pipeline for a Full Stack Cloud-Native Application. That means the Jenkins Pipeline
will include new Jenkins stages to statically analyze the Python, Golang and YAML code, in addition to the already analyzed Infrastructure as Code (Terraform, Kubernetes, Ansible, CloudFormation, Dockerfiles, etc).
This post will also explain how to consolidate all vulnerabilities/issues/bugs found and reports generated by all SAST Tools and Linters used in the CI/CD Pipeline.
Extra SAST Tools and Linters used
In this Jenkins Pipeline I am going to use the following SAST Tools/Linters:
- Yaml Linter: yamllint
- Golang Linter: golangci-lint
- Python Linter: Pylint
- IaC (Terraform, K8s, CloudFormation, Dockerfiles, etc): Kics, already used in the previous post
Extra Jenkins Plugins used
Also, these Jenkins Plugins:
- archiveArtifacts: required to archive build artifacts (war, zip or jar) so that they can be downloaded later. In our case, I’ll archive reports.
- publishHTML: required to publish HTML documents in Jenkins as a webserver. In our case, I’ll publish Kics’ report.
- Warnings-NG / recordIssues / tools: yamlLint, pyLint and goLint: similar to
publishHTML, but in this case I’ll import XML and Json reports and publish as HTML.
If you want to add more Linters because you added Java and NodeJS code, then you can find other linters in this list: Security along the SDLC for Cloud-Native Apps.
Integrating SAST in the Jenkins Pipeline for a Full Stack Application
Now, let’s create a new Pipeline, then copy the content of simple-ec2/_scripts/sast-pipeline-full-stack.groovy into Jenkins as a new Pipeline from Jenkins UI.
Once the new Pipeline has been created, you should click over Build with Parameters and enter a Git repository URL to be scanned by all above Linters, even Kics.
Some example Git repositories:
- AWS-CDK-Examples: A set of samples I used to experiment with AWS CDK. It contains Golang, Python, TypeScript, Dockerfile and YAML files.
- Vulnerability-Goapp: A vulnerable golang Web application for education.
- TerraGoat: It is a “Vulnerable by Design” Terraform repository.
- Sock Shop: It is a Microservice Demo Application.
Once the pipeline is running, you will see 4 new links in the Jenkins user interface sidebar, each of them being links to each Report that each SAST Tool or Linter has generated.
If you want to create this pipeline step by step, I recommend you follow this guide: https://github.com/chilcano/aws-cdk-examples/tree/main/simple-ec2
Conclusions
- Not all Projects are the same, you will need to know and identify the most appropriate SAST tools and Linter to build your CI/CD Pipelines with Static Security scanning tasks embedded.
- Consider standardising all SAST Tools and Linter Reports and findings on a single platform. Here I’ve used Jenkins Warnings-NG, which you can have a look at.
- You should be aware that this (SAST) is only a part of DevSecOps. DAST, IASP, etc. have yet to be implemented. However, at this point, your Cloud-Native Projects are already more secure.
References
- Security along the SDLC for Cloud-Native Apps - Posted on 2020/02/10
- SAST in your SDLC for Cloud-Native Apps - Part 1