SAST in your SDLC for Cloud-Native Apps
SAST stands for “Static Application Security Testing” and it is used to identify vulnerabilities by reviewing the source code. The best point or place to implement this kind of Security Testing is in early stages of your CI/CD Pipeline (Shift-left Testing). But What if you are building a Cloud Native Applications wich includes new artifacts or building blocks as Docker and/or Cloud Resources, what should do now to use SAST tools and techniques?. In this post, I will explain how to setup Jenkins on AWS to run a Pipeline with a SAST stage and everything using AWS CDK.
SAST in Cloud-Native Applications
Implement SAST in old-school or traditional Application was straight forward because you have to deal with a big block or a monolithic stack, but how to do the same with Cloud
Native Applications?. The answer is using as many SAST tools as different types of code, artifacts or building blocks compose your stack.
For example, a standard Cloud Native Application stack is composed of:
- Microservices in different languages (Python, Golang, PHP, …)
- REST and GraphQL APIs
- Docker containers (Dockerfile)
- Infrastructure as Code (Terraform, CloudFormation, Kubernetes manifests, …)
- Configuration code (Chef, Bash, Ansible, …)
Thus, for a satandard Cloud-Native Application, we are going to require 5 or less different SAST tools to review statically the code for each kind of code or artifact. Below I show a SAST tool list from which you can pick up any tool for convenience or based on your requirements.
Opensource SAST tools for Cloud-Native stacks
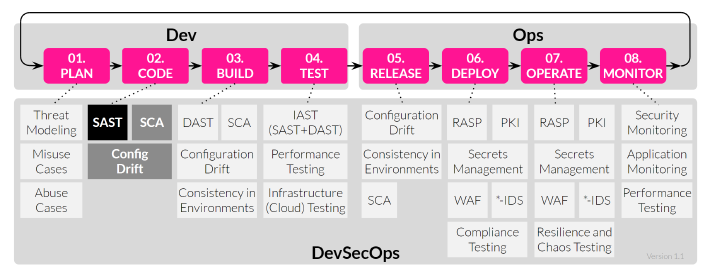
I’m going to list only a few SAST tools, but if you want to browse the full list, even DAST, IAST or RASP tools, you can check out my post about Security along the SDLC for Cloud-Native Apps.
| No. | SAST Tool | Vulnerability scanner for | |
|---|---|---|---|
| 1. | Anchore Grype |  |
Containers and filesystems |
| 2. | AquaSec Trivy |  |
Containers and application dependencies (Bundler, Composer, npm, yarn, etc) |
| 3. | AWS Cfn-Lint |  |
CloudFormation (.json, .yaml). Rules in Python |
| 4. | AWS Serverless Rules | Serverless Patterns in CloudFormation | |
| 5. | Bandit |  |
Python code |
| 6. | Checkmarx KICS |  |
Terraform (.tf, tfvars), CloudFormation (.json or .yaml), Ansible (.yaml), Dockerfile, K8s manifests, OpenAPI (.json or .yaml) |
| 7. | Checkov |  |
Terraform, CloudFormation, Kubernetes, Dockerfile, ARM Templates. |
| 8. | Clair |  |
Containers |
| 9. | Dagda | Containers and monitor Docker daemon | |
| 10. | Dockle |  |
Containers and support CIS Benchmarks |
| 11. | GolangCI-Lint |  |
Golang code |
| 12. | GoSec |  |
Golang code |
| 13. | huskyCI |  |
Orchestrate security test (Python, JS, Ruby, Tf, Golang, Java, …) and centralizes all results |
| 14. | PHPStan |  |
PHP code |
| 15. | Pylint |  |
Python code |
| 16. | Semgrep |  |
Works on 17+ languages. Write rules that look like your code. |
| 17. | Skyscanner CFrippe |  |
CloudFormation (.json, .yaml). Rules in Python |
| 18. | SonarQube CE |  |
Platform and carry out analysis of over 20 programming languages |
| 19. | SpotBugs |  |
Java. SpotBugs is the spiritual successor of FindBugs. |
| 20. | Stelligent cfn_nag |  |
CloudFormation (.json, .yaml). Rules in Ruby |
| 21. | Terraform Linter | Terraform (.tf, .tfvars) | |
| 22. | tfsec |  |
Terraform templates and support Terraform CDK. |
| - |
Designing the CI/CD Pipeline with a SAST stage
In this point we have a Cloud-Native Application that requires be statically scanned for security vulnerabilities, now is time to design and get ready our CI/CD Tooling. In order to embed the SAST process in your CI/CD pipeline, you will need at least 3 things:
- The CI/CD server
- It will orchestrate the multiple tasks (stages) defined in our CI/CD workflow.
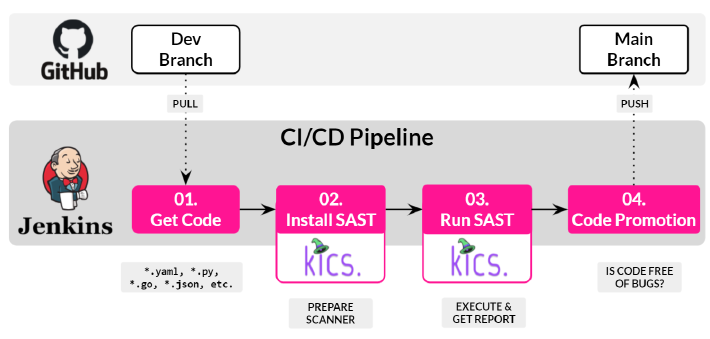
- A CI/CD workflow or pipeline is a sequence of tasks or stages. In this post, I’m going to use Jenkins with a pipeline with 4 stages: clone the GIT repository, run the SAST tools, get the report or outcomes and promote the code if the code is free of bugs.
- The SAST tool(s)
- It will allow us to scan for vulnerabilities in our IaC (Terraform, Ansible, CloudFormation, Docker, Kubernetes, etc.) used in the project.
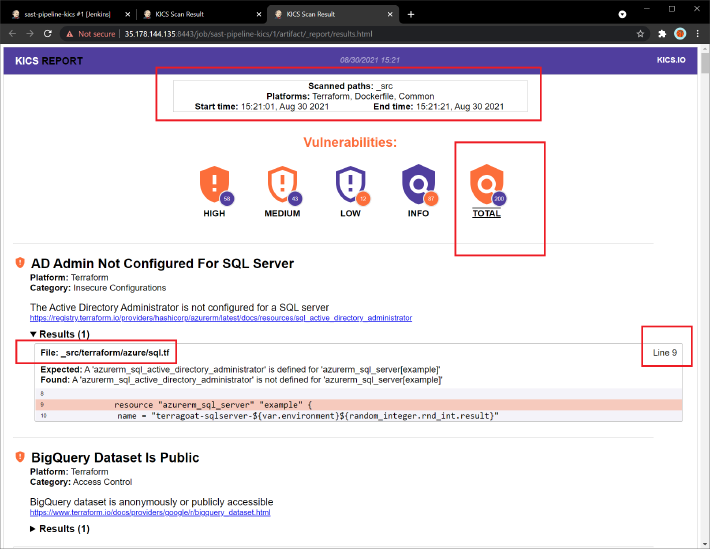
- As above, there are many SAST tool, each one is for each type of code. That means we will need one or more SAST tool. Although I could use AWS Cfn-Lint or AquaSec Trivy, I choose KICKS because It integrates multiple IaC Linters in one.
- The CI/CD portal server
- It will work as our web portal to consolidate all our outcomes in a single point.
- Initially, I wanted to use SonarQube, but unfortunatelly it has limitations to import third party generated reports, although It can be used as SAST tool as well, in this post I’m going to use Jenkins and HTML reports.
Implementing the CI/CD Pipeline with a SAST stage
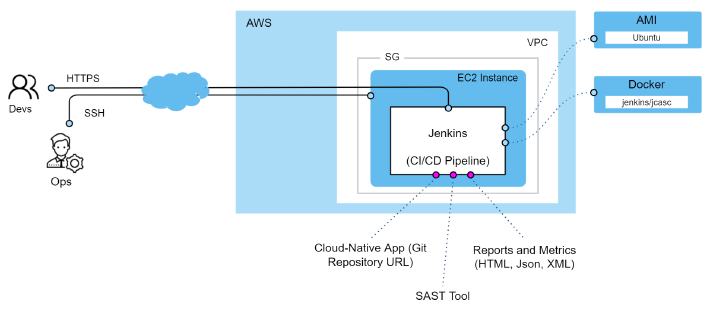
- I’m going to use AWS EC2 to deploy everything.
- Everything will be Dockerized.
- The Project I’m going to use as example will be TerraGoat, although you could use any kind of Cloud-Native Project, the only thing you need is provide the GitHub Repository URL when kicking off the Jenkins Pipeline.
Steps
I’ve created a Github repository with a CDK Project that automate the creation of AWS EC2 instance, with bash scripts to automate the installation of Jenkins and default plugins and a Jenkins Pipeline that includes SAST stages in the CI/CD process.
git clone https://github.com/chilcano/aws-cdk-examples.git
cd aws-cdk-examples/simple-ec2/
npm install @aws-cdk/aws-ec2 @aws-cdk/aws-iam dotenv
cdk deploy --profile es --require-approval never --outputs-file output.json
Further details can be found in the Chilcano/AWS-CDK-Examples GitHub repository.
Conclusions
-
Since that a Cloud-Native App stack is composed of multiple building blocks, artifacts and different programming languages, you will need SAST Tools for each of them, although that is not a problem, the hard part will be consolidate all outcomes comming from multiple SAST Tools in a single point, and then to make the right decisions during CI/CD-runtime (Jenkins runtime). Said that, SonarQube CE covers this part while you don’t have any approach in place yet, however importing third party reports into SonarQube is difficult.
-
Kics is a good SAST tool for Infrastructure as Code, It integrates multiple IaC Linters in one, but what if your project includes Golang code, Python code or Java code?. You will need to use other SAST Tools like GoSec, PyLint or Bandit, add a few stages to your Jenkins Pipeline and finally import all different reports generated for all SAST tools, even the Kics’ report, in a single point, correlate and track all vulnerabilities using a common criteria, etc, being that a real headache. At this point, Jenkins and Warnings-NG Plugin help a lot. In a next post I will explain how to do that.